Introduction
The Consumer IoT Security Road Map provides an overview of ETSI's world-leading work in consumer IoT security.
As more devices in our homes connect to the internet and as people entrust their personal data to an increasing number of services, the cyber security of the Internet of Things has become a growing concern. Poorly secured products threaten consumer’s privacy, and some devices are exploited by attackers to: launch large-scale DDoS cyber attacks, mine cryptocurrency and spy on users in their own homes. The first globally applicable standard for consumer IoT security was released by TC CYBER in 2019, achieving global adoption and sparking further TC CYBER work on an EN standard, an assessment specification, an implementation guide, and other vertical standards. This page describes these various packages of work from TC CYBER on IoT security.
Our Role & Activities
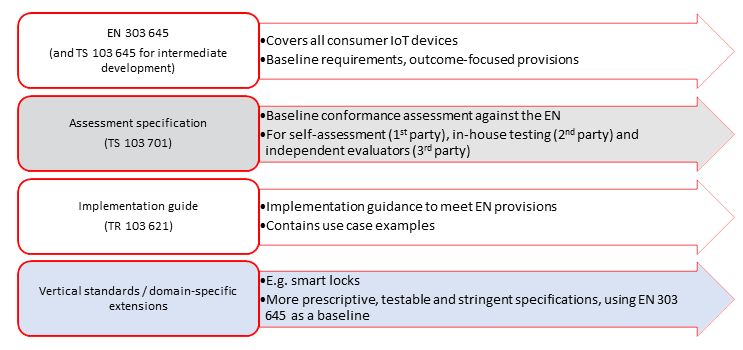
ETSI EN 303 645
The first globally applicable standard for consumer IoT was released by TC CYBER in February 2019 and was developed into ETSI EN 303 645, released in June 2020. ETSI EN 303 645 went through National Standards Organization comments and voting, engaging even more stakeholders in its development and ultimately strengthening the resulting standard. The EN is a result of collaboration and expertise from industry, academics and government. The original TS (TS 103 645) was updated to match the EN and is now used for development purposes only.
ETSI EN 303 645 is designed to prevent large-scale, prevalent attacks against smart devices that cybersecurity experts see every day, by establishing a security baseline for connected consumer products and provides a basis for future IoT certification schemes. This standard describes building security into IoT products from their design, rather than awkwardly bolting security measures on at the end.
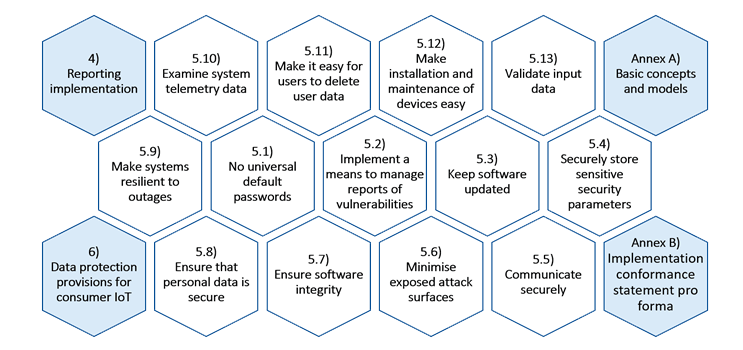
ETSI EN 303 645 supports a good security baseline for connected consumer products, provisioning a set of 13 recommendations, with the top three being: no default passwords, implement a vulnerability disclosure policy, and keep software updated. There are also specific data protection provisions for consumer IoT devices.
IoT products in scope include connected children’s toys and baby monitors, connected safety-relevant products such as smoke detectors and door locks, smart cameras, TVs and speakers, wearable health trackers, connected home automation and alarm systems, connected appliances (e.g. washing machines, fridges) and smart home assistants.
TC CYBER has worked closely with CEN/CENELEC JTC 13 members, who have made substantial contributions to ETSI EN 303 645, and the committee will continue to do so.
Assessment specification (TS 103 701)
The assessment specification, published in August 2021, specifies baseline conformance assessments for assessing consumer IoT products against the provisions of ETSI EN 303 645. Its purpose is to test against the provisions of EN 303 645; it does not extend EN 303 645 in any way. It sets out mandatory and recommended assessments, intended to be used by testing labs and certifying bodies that provide assurance on the security of relevant products, as well as manufacturers that wish to carry out a self-assessment. The assurance schemes that this document is used in, and their outcomes, are out of scope. However, the TS 103 701 is intended as input to a future EU common cybersecurity certification scheme as proposed in the Cybersecurity Act.
Implementation guide (TR 103 621)
The implementation guide, started in June 2020, gives easy-to-use guidance to help manufacturers and other stakeholders to meet the provisions defined for Consumer IoT devices in ETSI EN 303 645. It includes a non-exhaustive set of example implementations – obviously not all possible implementations will be included! – that meet the provisions in the EN.
Vertical standards
ETSI EN 303 645 provides a useful security baseline that spans a variety of consumer IoT devices, but sometimes additional sector-specific requirements need to be stipulated to standardise device security. TC CYBER supports new work items to create sector-specific standards (adding provisions to ETSI EN 303 645 or TS 103 701) to create a new vertical standard for a sector. For this purpose, TC CYBER created templates providing a structured way to extend ETSI EN 303 645 and ETSI TS 103 701 into a vertical domain, with adapted or new provisions in cyber security and data protection and their testing. Even if it is not an IoT device, the generic character of EN 303 645 made it appropriate as a baseline for a TS on Home Gateway Security (TS 103 848). Currently, TC CYBER is working on other verticals like smart door locks and voice-controlled devices, based on ETSI EN 303 645.
Coordinated Vulnerability Disclosure
As mandated in EN 303 645, implementing a vulnerability disclosure policy is a key requirement in ensuring on-going strong cyber security after a product has been placed on the market. ETSI TR 103 838 provides a guide to coordinated vulnerability disclosure. It contains generic advice on how to respond to and manage a vulnerability disclosure, a defined triage process, advice on managing vulnerabilities in third party products or suppliers. It also includes an example of a vulnerability disclosure policy.
National schemes development and alignment
ETSI EN 303 645 is a cohesive standard that presents an achievable, single target for manufacturers and IoT stakeholders to attain. Many countries have already based their national product certification schemes around the EN and its predecessor TS. It demonstrates how one standard can underpin many assurance schemes and provide flexibility in certification - whilst maintaining world-leading security.
- Finland’s national consumer IoT certification scheme
- Germany BSI IoT label
- Singapore’s national Cybersecurity Labelling Scheme
- India TEC Code of Practice for Securing Consumer IoT
- Vietnam’s Cyber Information Security Requirements for Internet of things
- U.K.’s Product Security and Telecommunications Infrastructure Bill
- Australia Code of Practice - Securing the Internet of Things for Consumers
In addition to schemes, some organizations provide a translation to foster adoption, e.g. the Japanese Information-technology Promotion Agency.
Two websites provide additional valuable information:
Not only EN 303 645 can be used by national schemes, but it can also facilitate alignment across jurisdictions. Countries started signing mutual recognition agreements such as Singapore with Finland and Germany.
A first-time multistakeholder collaboration convened by the World Economic Forum has recognized the risks, and formed a global consensus for baseline IoT security measures to protect consumers with five requirements from ETSI EN 303 645.
Within Europe, EN 303 645 and the assessment specification TS 103 701 are well placed to provide the foundation for “basic”-level IoT assurance in an EU Cybersecurity Act (CSA) scheme. EN 303 645 was originally developed for the CSA and is not suitable for direct transposition as a Harmonised Standard under EU product legislation like RED or the EU Cyber Resilience Act. EN 303 645 could inform future separate Harmonised Standard(s) on security, along with other applicable ETSI deliverables.
 Private Schemes
Private Schemes
Many organizations have already based their products and international private certification schemes around the EN and its predecessor TS. It demonstrates how one standard can underpin many assurance schemes and provide flexibility in certification - whilst maintaining world-leading security.
- PSA Certified (backed by Arm)
- The Global Certification Forum
- TÜV Süd testing
- TÜV Rheinland worldwide testing and certification
- VDE institue testing
- SESIP by Global Platform mapped
- SGS IoT Testing and Conformity Assessment Program
- DEKRA security evaluations
- UL's IoT security Rating assesment, verification and labelling solution
- SafesShark and BSI IoT cyber security assessments, testing and certification
- Bureau Veritas Type Certification for IoT Devices
- ioXt's development of an assurance profile
- Intertek’s Cyber Assured certification
And many more: Eurosmart, KIWA, Secura, Nemko, ACCS, IASME…
Current and future work
There are four steps for device and component manufacturers to implement EN 303 645:

1. Review concepts:
- Review definitions in the EN
- Review information in Annex A on device architectures, network architectures, and device states.
2. Implement the provisions:
- Shall implement all 33 requirements
- Should implement all 35 recommendations
- Shall record rationale if a recommendation is not implemented (Annex B)
- Refer to the implementation guide (TR 103 621) for further guidance
3. Conformance statement: Complete Annex B (implementation conformance pro forma)
4. Assessment: prepare for assessment (in-house or external) using the assessment specification (TS 103 701)
Useful links
For more on ETSI's security work, check out the cyber security page on our website.
See also:
- ETSI TR 103 621, March 2022
- ETSI EN 303 645 V2.1.1, June 2020
- ETSI TS 103 645 V3.1.1, January 2024
- ETSI TS 103 701, August 2021
- ETSI EN 303 645 Press Release, June 2020
- ETSI TS 103 645 Press Release, February 2019
- Template for Consumer IoT Derivative work
- TC CYBER's Roadmap for other TC CYBER work and projects

 Private Schemes
Private Schemes